Researchers have observed a new post-exploitation attack framework used in the wild, named Manjusaka, which can be deployed as an alternative to the widely abused Cobalt Strike toolset or parallel to it for redundancy.
Manjusaka uses implants written in the cross-platform Rust programming language, while its binaries are written in the equally versatile GoLang.
Its RAT (remote access trojan) implants support command execution, file access, network reconnaissance, and more, so hackers can use it for the same operational goals as Cobalt Strike.
Campaign and discovery
Manjusaka was discovered by researchers at Cisco Talos, who were called to investigate a Cobalt Strike infection on a customer, so the threat actors used both frameworks in that case.
The infection came via a malicious document masquerading as a report about a COVID-19 case in Golmud City in Tibet for contact tracing.
The document featured a VBA macro that executes through rundll32.exe to fetch a second-stage payload, Cobalt Strike, and load it in memory.
However, instead of just using Cobalt Strike as their primary attack toolkit, they used it to download Manjusaka implants, which depending on the host's architecture, can be either EXE (Windows) or ELF files (Linux).
"Cisco Talos recently discovered a new attack framework called "Manjusaka" being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework," warns the Cisco Talos researchers.
Manjusaka capabilities
Both Windows and Linux versions of the implant feature almost the same capabilities and implement similar communication mechanisms.
The implants comprise a RAT and a file management module, each featuring distinct capabilities.
The RAT supports arbitrary command execution via “cmd.exe”, collects credentials stored in web browsers, WiFi SSID and passwords, and discovers network connections (TCP and UDP), account names, local groups, etc.
.png) Manjusaka command execution system (Cisco)
Manjusaka command execution system (Cisco)Moreover, it can steal Premiumsoft Navicat credentials, capture screenshots of the current desktop, list running processes, and even check hardware specs and thermals.
The file management module can perform file enumeration, create directories, obtain full file paths, read or write file contents, delete files or directories, and move files between locations.
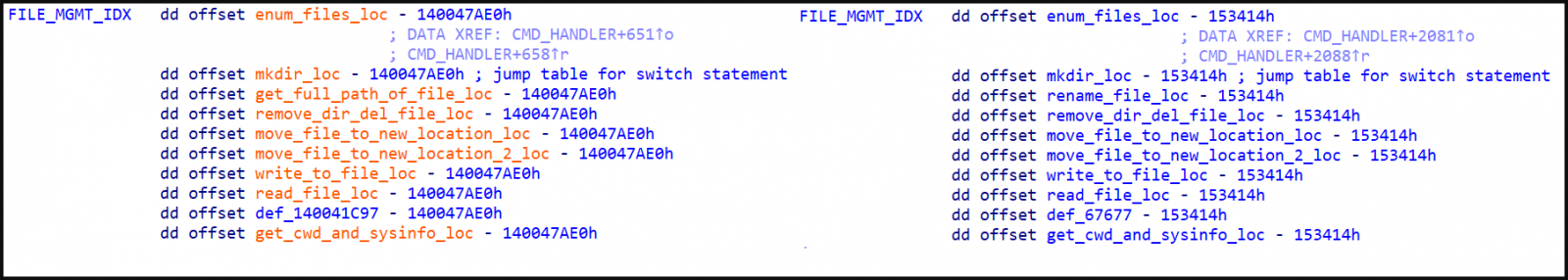 File management capabilities, EXE left, ELF right (Cisco)
File management capabilities, EXE left, ELF right (Cisco)A shift in tools
Right now, it looks like Manjusaka is tentatively deployed in the wild for testing, so its development is likely not in its final phases. However, the new framework is already powerful enough for real-world use.
Cisco notes that its researchers found a design diagram on a promotional post by the malware author, depicting components that weren’t implemented in the sampled versions.
This means that they’re not available in the “free” version used in the analyzed attack or haven’t been completed by the author yet.
“This new attack framework contains all the features that one would expect from an implant, however, it is written in the most modern and portable programming languages.
The developer of the framework can easily integrate new target platforms like MacOSX or more exotic flavors of Linux as the ones running on embedded devices.
The fact that the developer made a fully functional version of the C2 available increases the chances of wider adoption of this framework by malicious actors.” - Cisco Talos
The lure document is written in Chinese, and the same applies to the malware's C2 menus and configuration options, so it is safe to assume that its developers are based in China. Talos' OSINT narrowed their location to the Guangdong region.
If that's indeed the case, we might see Manjusaka deployed in the campaigns of multiple Chinese APTs soon, as threat groups from the country are known for sharing a common toolset.
Recently, we reported about the rise of a post-exploitation toolkit named 'Brute Ratel,' which was also meant to replace the now aged and more easily detectable cracked versions of Cobalt Strike.
Threat actors are expected to continue moving away from Cobalt Strike gradually, and many alternative attack frameworks will likely appear, attempting to grow into the new market opportunity.


 2 years ago
134
2 years ago
134