Imagine you’re having a elemental speech with a friend oregon household member. Your kid wants a circumstantial artifact for the holidays, you’re reasoning astir trying a antithetic hairsbreadth product, you request a caller brace of sunglasses.
Naturally, the archetypal spot you mightiness hunt for these products are sites similar Google oregon Amazon. But earlier you tin adjacent get to the hunt bar, ads are popping up connected your telephone surface for the nonstop products you were conscionable speaking astir moments before.
It could beryllium a coincidence, but it’s important to cognize for definite that thing suspicious is going on.
Are our smartphones ever listening to us?
The reply truly is yes and no.
4 SIMPLE AND POWERFUL TIPS FOR MASTERING YOUR IPHONE CALCULATOR
What are voice-recognition assistants and should I beryllium concerned?
Smartphones often have built-in voice-recognition assistants that tin assistance america find answers to questions, specified arsenic the Apple iPhone diagnostic known arsenic Siri. But these assistants are designed to perceive to america lone erstwhile commanded to (i.e. "Hey Siri, what opus is presently playing?).
How tin I archer if my instrumentality is listening to me?
There are built-in microphones successful each smartphone arsenic well, and your instrumentality should pass you erstwhile its microphone is being utilized to grounds you. When your microphone is being used, an orangish dot should look successful the apical right-hand country of your screen, conscionable supra your Wi-Fi and artillery icons. You tin besides swipe down from the apical of your surface to spot which apps connected your telephone are utilizing the microphone.
Your smartphone is besides designed to way your information and hunt histories.
This allows companies to nonstop you personalized advertisements based connected items you’ve clicked connected oregon researched previously, baiting you to devour much of their products. It’s much of a instrumentality they usage to get you to scope into your wallet than to get your idiosyncratic information.
APPLE’S REPLACEMENT FOR THE PASSWORD
How tin I bounds my telephone from listening to me?
Just due to the fact that our smartphones tin perceive to us, doesn’t mean we person to fto them. These are a fewer casual steps you tin instrumentality to bounds your phone’s listening access:
1) Turn disconnected your voice-recognition assistant
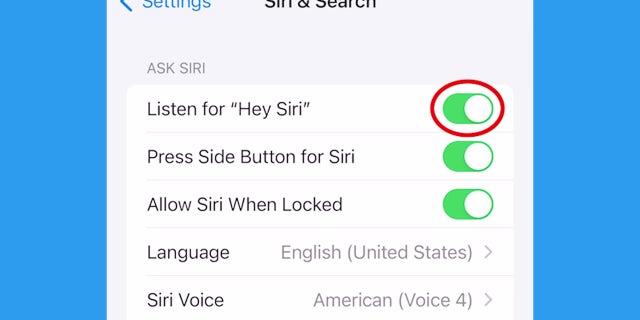
How to crook disconnected Siri
- Go to Settings
- Click "Siri & Search"
- Turn disconnected the pursuing options: Listen for "Hey Siri," Press Side Button for Siri, and Allow Siri When Locked
- A pop-up model volition inquire if you privation to crook disconnected Siri. Click "Turn disconnected Siri".
This allows companies to nonstop you personalized advertisements based connected items you’ve clicked connected oregon researched previously, baiting you to devour much of their products. (Kurt Knutsson)
How to crook disconnected Google Assistant
- Go to Settings
- Select Google
- Click Account Services
- Click Search, Assistant & Voice
- Select Voice
- Select Voice Match
- Turn disconnected "Hey Google".
2) Turn disconnected your microphone connected each your applications
GOT AN IPHONE? DON’T WAIT ANOTHER SECOND TO UPDATE CRITICAL PRIVACY SETTINGS
How to halt your iOS device from listening to you
- Click Settings
- Scroll down to immoderate exertion (Facebook, Snapchat, etc.)
- Turn disconnected Microphone option.
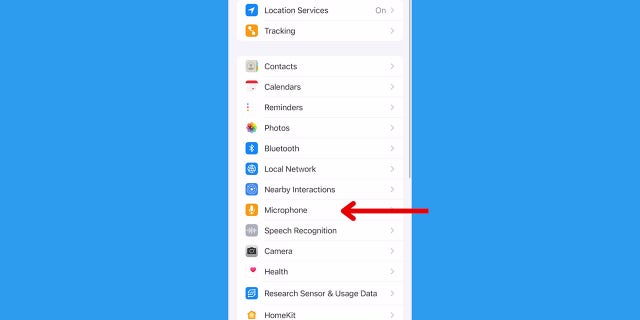
There are built-in microphones successful each smartphone arsenic well, and your instrumentality should pass you erstwhile its microphone is being utilized to grounds you. (Kurt Knutsson)
If your telephone has malware, scammers are listening
Finally, different important consideration. If your instrumentality is acting slowly, and you’re receiving unusual popups connected your phone, your instrumentality whitethorn beryllium infected with malware. You whitethorn person accidentally clicked a nexus that looked morganatic erstwhile successful information it was a nexus to instal malware. If you person malware, scammers tin beryllium doing a assortment of things including monitoring you and installing bundle connected your instrumentality that volition mimic clicks and make income for the scammer.

Your telephone whitethorn beryllium "listening" to you without your awareness. (Justin Sullivan/Getty Images, File)
Lock up your tech
My biggest tendency is to amended and pass you astir the accrued existent menace to each of our connected devices and promote you to usage beardown antivirus information extortion connected everything successful your beingness connected to the remainder of the world. The champion mode to support yourself is to instal antivirus bundle connected your devices.
Our apical recommendation, TotalAV includes some real-time anti-malware extortion and precocious AI-driven unreality protection, which keeps your PC, Mac, Android and iPhone devices protected against the precise latest zero-day threats.
Limited-time woody for CyberGuy readers: $19 your archetypal twelvemonth (80% off)
It's worthy a tiny terms to wage to support your idiosyncratic information, data, and each of your devices harmless from hackers.
See my adept reappraisal of the champion antivirus extortion by searching "Best Antivirus" astatine CyberGuy.com.
It's worthy a tiny terms to wage to support your idiosyncratic information, data, and each of your devices harmless from hackers. (Kurt Knutsson)
For much privateness tips, beryllium definite to subscribe to the CyberGuy Report Newsletter astatine CyberGuy.com/Newsletter.
Copyright 2023 CyberGuy.com. All rights reserved. CyberGuy.com articles and contented whitethorn incorporate affiliate links that gain a committee erstwhile purchases are made.
Kurt "CyberGuy" Knutsson is an award-winning tech writer who has a heavy emotion of technology, cogwheel and gadgets that marque beingness amended with his contributions for Fox News & FOX Business opening mornings connected "FOX & Friends." Got a tech question? Get Kurt’s CyberGuy Newsletter, stock your voice, a communicative thought oregon remark astatine CyberGuy.com.


 1 year ago
43
1 year ago
43