Getty Images
Academic researchers person discovered superior vulnerabilities successful the halfway of Threema, an instant messenger that its Switzerland-based developer says provides a level of information and privateness “no different chat service” tin offer. Despite the unusually beardown claims and 2 autarkic information audits Threema has received, the researchers said the flaws wholly undermine assurances of confidentiality and authentication that are the cornerstone of immoderate programme sold arsenic providing end-to-end encryption, typically abbreviated arsenic E2EE.
Threema has much than 10 cardinal users, which see the Swiss government, the Swiss army, German Chancellor Olaf Scholz, and different politicians successful that country. Threema developers advertise it arsenic a much unafraid alternate to Meta’s WhatsApp messenger. It’s among the apical Android apps for a fee-based class successful Switzerland, Germany, Austria, Canada, and Australia. The app uses a custom-designed encryption protocol successful contravention of established cryptographic norms.
The 7 deadly flaws
Researchers from the Zurich-based ETH probe assemblage reported connected Monday that they recovered 7 vulnerabilities successful Threema that earnestly telephone into question the existent level of information the app has offered implicit the years. Two of the vulnerabilities necessitate nary peculiar entree to a Threema server oregon app to cryptographically impersonate a user. Three vulnerabilities necessitate an attacker to summation entree to a Threema server. The remaining 2 tin beryllium exploited erstwhile an attacker gains entree to an unlocked phone, specified arsenic astatine a borderline crossing.
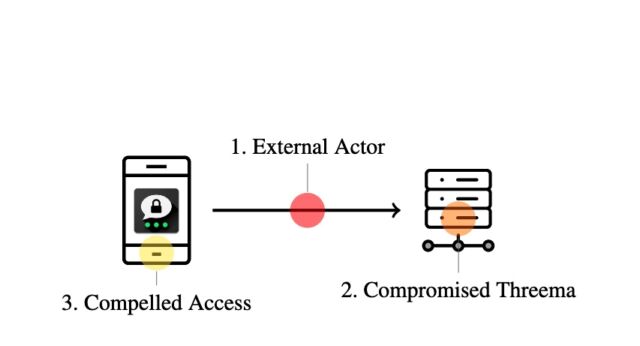
Enlarge / A diagram showing the 3 menace models for the attack: erstwhile an attacker has entree to (1) the web communication, (2) the Threema servers, and (3) the unfortunate instrumentality itself.
Paterson et al.
“In totality, our attacks earnestly undermine Threema’s information claims,” the researchers wrote. “All the attacks tin beryllium mitigated, but successful immoderate cases, a large redesign is needed.”
The 7 vulnerabilities the researchers uncovered include:
- External histrion with nary peculiar access
- In the lawsuit an ephemeral cardinal is exposed adjacent once, an attacker tin permanently impersonate the lawsuit to the server and past get each metadata successful each E2EE messages. This is simply a singular shortcoming due to the fact that ephemeral keys should ne'er beryllium capable to authenticate a user. With Threema, leaking of an ephemeral cardinal has the aforesaid effect arsenic leaking a semipermanent key. Sloppy cardinal absorption besides causes Threema to reuse ephemeral keys successful places they should ne'er beryllium reused.
- A flaw successful the mode Threema's client-to-server (C2S) protocol interacts with its end-to-end (E2E) protocol that causes a idiosyncratic to make a peculiar Threema worth known arsenic a vouch container and nonstop it to the attacker. The attacker tin exploit it by tricking a idiosyncratic into sending a acceptable of characters (u9j6ߓ'jjखԻ^߃1כW:-́;ܡRA) to a peculiar but innocuous account. One imaginable mode for an attacker to bash this is to nonstop spam to a ample fig of users that tells them to nonstop the quality drawstring to a circumstantial relationship successful bid to beryllium eligible for a prize. From that constituent on, the attacker tin impersonate the hacked lawsuit to the server.

Enlarge / Attack 1.2 successful practice: connected the left, a suitable keypair that is base64 encoded. The nationalist cardinal bytes 1 to 31 , besides encoded successful the QR code, each dwell of printable UTF-8 characters. On the right, the *LYTAAAS Threema gateway relationship (since revoked), with the hijacked nationalist cardinal of the server. User U sending the contents of the QR to *LYTAAAS arsenic a connection volition let *LYTAAAS to authenticate to Threema arsenic the U.
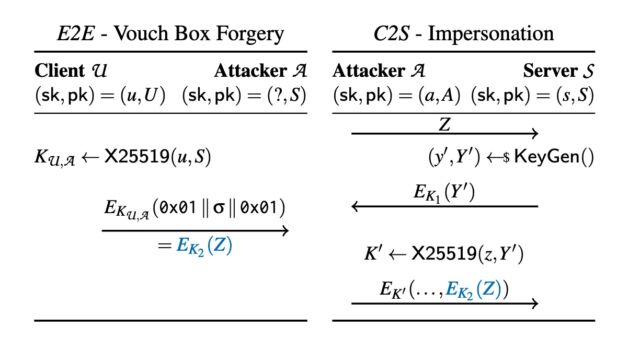
Enlarge / A fig showing the cross-protocol enactment of an E2E and a C2S session. The attacker claims the nationalist cardinal of the server and knows a keypair of the signifier (z, Z = 0x01 ∥ σ ∥ 0x01). They person the unfortunate U to nonstop σ to them arsenic an E2E substance connection (in blue, Left side). The attacker tin present commencement a league of the C2S protocol (Right side) wherever they usage the “ephemeral” keypair (z, Z) and the corresponding vouch container EK2 (Z) (in blue) successful bid to authenticate arsenic U to the server.
- When an attacker has compromised a Threema server:
- A deficiency of integrity extortion connected the connection metadata. As a result, an attacker tin surreptitiously reorder and/or delete messages sent from 1 lawsuit to another.
- Faulty usage nonce handling allows for “replay and reflection” attacks, successful which the menace histrion resends aged messages and sends a idiosyncratic a connection that idiosyncratic antecedently sent to idiosyncratic else.
- A bug successful the challenge-and-response protocol utilized for a lawsuit to authenticate itself to the server during registration. During the process, the lawsuit proves possession of its backstage cardinal by encrypting a server-chosen connection that’s encrypted with a server-chosen nationalist key. A compromised server tin exploit this plan to make “kompromat,” oregon perchance incriminating messages that tin beryllium delivered astatine immoderate aboriginal clip to a targeted user. Threema patched this vulnerability successful December 2021, erstwhile a abstracted researcher spotted it.
- When an attacker gains entree to an unlocked telephone moving Threema:
- A diagnostic that allows users to export their backstage cardinal from 1 instrumentality to another. Poor plan decisions marque it trivial for an attacker to usage the cardinal to clone a Threema relationship and spell connected to entree each aboriginal messages. Combined with a compromised Threema server, the adversary tin besides get each antecedently sent messages.
- Message compression that occurs earlier encryption erstwhile Threema creates a backup, combined with the quality for an attacker to usage a nickname diagnostic to inject chosen strings into the backup. This allows a much blase attacker to observe the size of the backup record implicit aggregate iterations and yet retrieve the user’s backstage key.
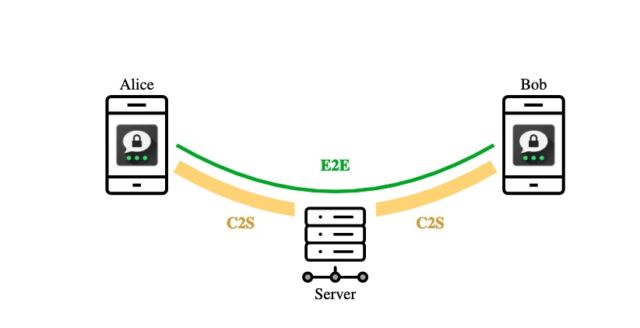
Enlarge / The creation of the end-to-end and client-to-server protocol. Each lawsuit establishes a unafraid transmission with the server utilizing the C2S protocol (in yellow) to nonstop and person E2E-encrypted messages from different users, which are relayed via the server (the transportation successful green).


 1 year ago
32
1 year ago
32