Getty Images
Researchers person unearthed never-before-seen malware that hackers from North Korea person been utilizing to surreptitiously work and download email and attachments from infected users' Gmail and AOL accounts.
The malware, dubbed SHARPEXT by researchers from information steadfast Volexity, uses clever means to instal a browser hold for the Chrome and Edge browsers, Volexity reported successful a blog post. The hold can't beryllium detected by the email services, and since the browser has already been authenticated utilizing immoderate multifactor authentication protections successful place, this progressively fashionable information measurement plays nary relation successful reining successful the relationship compromise.
The malware has been successful usage for "well implicit a year," Volexity said, and is the enactment of a hacking radical the institution tracks arsenic SharpTongue. The radical is sponsored by North Korea's authorities and overlaps with a group tracked arsenic Kimsuky by different researchers. SHARPEXT is targeting organizations successful the US, Europe, and South Korea that enactment connected atomic weapons and different issues North Korea deems important to its nationalist security.
Volexity President Steven Adair said successful an email that the hold gets installed "by mode of spear phishing and societal engineering wherever the unfortunate is fooled into opening a malicious document. Previously we person seen DPRK menace actors motorboat spear phishing attacks wherever the full nonsubjective was to get the unfortunate to instal a browser hold vs it being a station exploitation mechanics for persistence and information theft." In its existent incarnation, the malware works lone connected Windows, but Adair said there's nary crushed it couldn't beryllium broadened to infect browsers moving connected macOS oregon Linux, too.
The blog station added: "Volexity's ain visibility shows the hold has been rather successful, arsenic logs obtained by Volexity amusement the attacker was capable to successfully bargain thousands of emails from aggregate victims done the malware's deployment."
Installing a browser hold during a phishing cognition without the end-user noticing isn't easy. SHARPEXT developers person intelligibly paid attraction to probe similar what's published here, here, and here, which shows however a information mechanics successful the Chromium browser motor prevents malware from making changes to delicate idiosyncratic settings. Each clip a morganatic alteration is made, the browser takes a cryptographic hash of immoderate of the code. At startup, the browser verifies the hashes, and if immoderate of them don't match, the browser requests the aged settings beryllium restored.
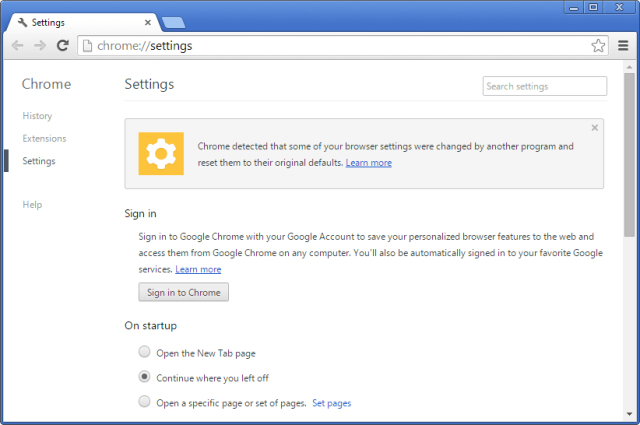
For attackers to enactment astir this protection, they indispensable archetypal extract the pursuing from the machine they're compromising:
- A transcript of the resources.pak record from the browser (which contains the HMAC effect utilized by Chrome)
- The user's S-ID value
- The archetypal Preferences and Secure Preferences files from the user's system
After modifying the penchant files, SHARPEXT automatically loads the hold and executes a PowerShell publication that enables DevTools, a mounting that allows the browser to tally customized codification and settings.
"The publication runs successful an infinite loop checking for processes associated with the targeted browsers," Volexity explained. "If immoderate targeted browsers are recovered running, the publication checks the rubric of the tab for a circumstantial keyword (for example' 05101190,' oregon 'Tab+' depending connected the SHARPEXT version). The circumstantial keyword is inserted into the rubric by the malicious hold erstwhile an progressive tab changes oregon erstwhile a leafage is loaded."
Volexity
The station continued:
The keystrokes sent are equivalent to Control+Shift+J, the shortcut to alteration the DevTools panel. Lastly, the PowerShell publication hides the recently opened DevTools model by utilizing the ShowWindow() API and the SW_HIDE flag. At the extremity of this process, DevTools is enabled connected the progressive tab, but the model is hidden.
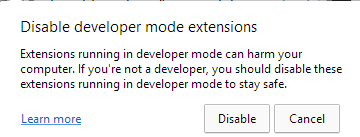
In addition, this publication is utilized to fell immoderate windows that could alert the victim. Microsoft Edge, for example, periodically displays a informing connection to the idiosyncratic (Figure 5) if extensions are moving successful developer mode. The publication perpetually checks if this model appears and hides it by utilizing the ShowWindow() and the SW_HIDE flag.
Volexity
Once installed, the hold tin execute the pursuing requests:
| HTTP POST Data | Description |
| mode=list | List antecedently collected email from the unfortunate to guarantee duplicates are not uploaded. This database is continuously updated arsenic SHARPEXT executes. |
| mode=domain | List email domains with which the unfortunate has antecedently communicated. This database is continuously updated arsenic SHARPEXT executes. |
| mode=black | Collect a blacklist of email senders that should beryllium ignored erstwhile collecting email from the victim. |
| mode=newD&d=[data] | Add a domain to the database of each domains viewed by the victim. |
| mode=attach&name=[data]&idx=[data]&body=[data] | Upload a caller attachment to the distant server. |
| mode=new&mid=[data]&mbody=[data] | Upload Gmail information to the distant server. |
| mode=attlist | Commented by the attacker; person an attachments database to beryllium exfiltrated. |
| mode=new_aol&mid=[data]&mbody=[data] | Upload AOL information to the distant server. |
SHARPEXT allows the hackers to make lists of email addresses to disregard and to support way of email oregon attachments that person already been stolen.
Volexity created the pursuing summary of the orchestration of the assorted SHARPEXT components it analyzed:

Volexity
The blog station provides images, record names, and different indicators that trained radical tin usage to find if they person been targeted oregon infected by this malware. The institution warned that the menace it poses has grown implicit clip and isn't apt to spell distant anytime soon.
"When Volexity archetypal encountered SHARPEXT, it seemed to beryllium a instrumentality successful aboriginal improvement containing galore bugs, an denotation the instrumentality was immature," the institution said. "The latest updates and ongoing attraction show the attacker is achieving its goals, uncovering worth successful continuing to refine it."


 2 years ago
121
2 years ago
121