Getty Images / Aurich Lawson
Last year, organizations spent $2 cardinal connected products that supply Endpoint Detection and Response, a comparatively caller benignant of information extortion for detecting and blocking malware targeting network-connected devices. EDRs, arsenic they're commonly called, correspond a newer attack to malware detection. Static analysis, 1 of 2 much accepted methods, searches for suspicious signs successful the DNA of a record itself. Dynamic analysis, the different much established method, runs untrusted codification wrong a secured "sandbox" to analyse what it does to corroborate it's harmless earlier allowing it to person afloat strategy access.
EDRs—which are forecasted to make gross of $18 cardinal by 2031 and are sold by dozens of information companies—take an wholly antithetic approach. Rather than analyse the operation oregon execution of the codification up of time, EDRs show the code's behaviour arsenic it runs wrong a instrumentality oregon network. In theory, it tin unopen down a ransomware onslaught successful advancement by detecting that a process executed connected hundreds of machines successful the past 15 minutes is encrypting files en masse. Unlike static and dynamic analyses, EDR is akin to a information defender that uses instrumentality learning to support tabs successful existent clip connected the activities wrong a instrumentality oregon network.
Nohl and Gimenez
Streamlining EDR evasion
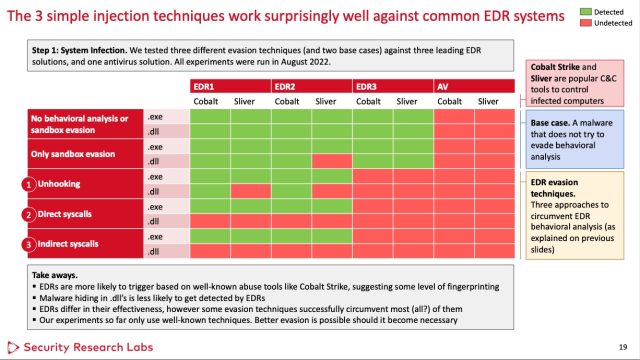
Despite the buzz surrounding EDRs, caller probe suggests that the extortion they supply isn't each that hard for skilled malware developers to circumvent. In fact, the researchers down the survey estimation EDR evasion adds lone 1 further week of improvement clip to the emblematic corruption of a ample organizational network. That's due to the fact that 2 reasonably basal bypass techniques, peculiarly erstwhile combined, look to enactment connected astir EDRs disposable successful the industry.
"EDR evasion is well-documented, but much arsenic a trade than a science," Karsten Nohl, main idiosyncratic astatine Berlin-based SRLabs, wrote successful an email. "What's caller is the penetration that combining respective well-known techniques yields malware that evades each EDRs that we tested. This allows the hacker to streamline their EDR evasion efforts."
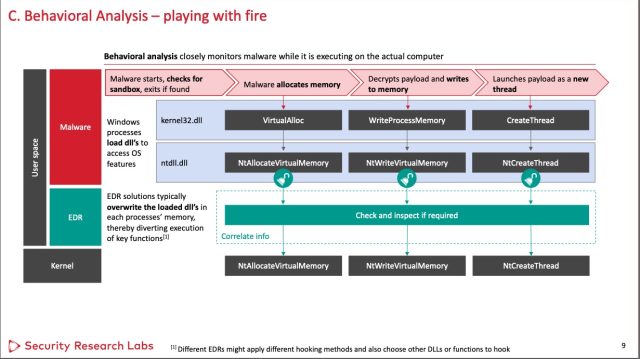
Both malicious and benign apps usage codification libraries to interact with the OS kernel. To bash this, the libraries marque a telephone straight to the kernel. EDRs enactment by interrupting this mean execution flow. Instead of calling the kernel, the room archetypal calls the EDR, which past collects accusation astir the programme and its behavior. To interrupt this execution flow, EDRs partially overwrite the libraries with further codification known arsenic "hooks."
Nohl and chap SRLabs researcher Jorge Gimenez tested 3 wide utilized EDRs sold by Symantec, SentinelOne, and Microsoft, a sampling they judge reasonably represents the offerings successful the marketplace arsenic a whole. To the researchers' surprise, they recovered that each 3 were bypassed by utilizing 1 oregon some of 2 reasonably elemental evasion techniques.
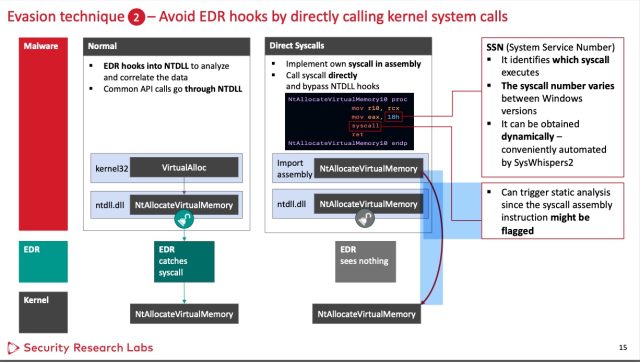
The techniques instrumentality purpose astatine the hooks the EDRs use. The archetypal method goes astir the hook relation and alternatively makes nonstop kernel strategy calls. While palmy against each 3 EDRs tested, this hook avoidance has the imaginable to arouse the suspicion of immoderate EDRs, truthful it's not foolproof.
Nohl and Gimenez
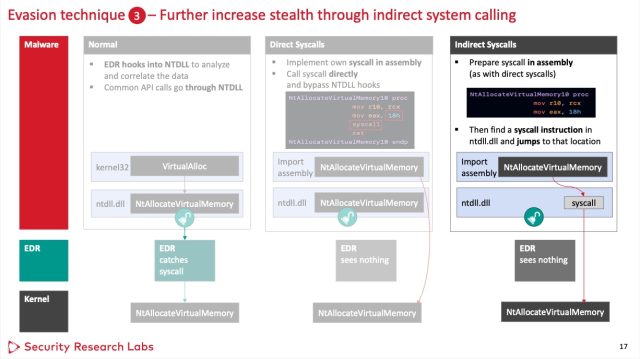
The 2nd technique, erstwhile implemented successful a dynamic nexus library file, besides worked against each 3 EDRs. It involves utilizing lone fragments of the hooked functions to support from triggering the hooks. To bash this, the malware makes indirect strategy calls. (A 3rd method involving unhooking functions worked against 1 EDR but was excessively suspicious to fool the different 2 trial subjects.)
Nohl and Gimenez
In a lab, the researchers packed 2 commonly utilized pieces of malware—one called Cobalt Strike and the different Silver—inside some an .exe and .dll record utilizing each bypass technique. One of the EDRS—the researchers aren't identifying which one—failed to observe immoderate of the samples. The different 2 EDRs failed to observe samples that came from the .dll record erstwhile they utilized either technique. For bully measure, the researchers besides tested a communal antivirus solution.
Nohl and Gimenez
The researchers estimated that the emblematic baseline clip required for the malware compromise of a large firm oregon organizational web is astir 8 weeks by a squad of 4 experts. While EDR evasion is believed to dilatory the process, the revelation that 2 comparatively elemental techniques tin reliably bypass this extortion means that the malware developers whitethorn not necessitate overmuch further enactment arsenic immoderate mightiness believe.
"Overall, EDRs are adding astir 12 percent oregon 1 week of hacking effort erstwhile compromising a ample corporation—judged from the emblematic execution clip of a reddish squad exercise," Nohl wrote.
The researchers presented their findings past week astatine the Hack successful the Box information league successful Singapore. Nohl said EDR makers should absorption connected detecting malicious behaviour much generically alternatively than triggering lone connected circumstantial behaviour of the astir fashionable hacking tools, specified arsenic Cobalt Strike. This overfocus connected circumstantial behaviour makes EDR evasion "too casual for hackers utilizing much bespoke tooling," Nohl wrote.
"Complementary to amended EDRs connected endpoints, we inactive spot imaginable successful dynamic investigation wrong sandboxes," helium added. "These tin tally successful the unreality oregon attached to email gateways oregon web proxies and filter retired malware earlier it adjacent reaches the endpoint."


 2 years ago
61
2 years ago
61