Intel
Intel’s latest procreation of CPUs contains a vulnerability that allows attackers to get encryption keys and different confidential accusation protected by the company’s bundle defender extensions, the precocious diagnostic that acts arsenic a integer vault for information users’ astir delicate secrets.
Abbreviated arsenic SGX, the extortion is designed to supply a fortress of sorts for the safekeeping of encryption keys and different delicate data, adjacent erstwhile the operating strategy oregon a virtual instrumentality moving connected apical is maliciously compromised. SGX works by creating trusted execution environments that support delicate codification and the information it works with from monitoring oregon tampering by thing other connected the system.
Cracks successful Intel’s foundational security
SGX is simply a cornerstone of the information assurances galore companies supply to users. Servers utilized to grip interaction find for the Signal Messenger, for instance, trust connected SGX to guarantee the process is anonymous. Signal says moving its precocious hashing strategy provides a “general look for doing backstage interaction find successful SGX without leaking immoderate accusation to parties that person power implicit the machine, adjacent if they were to connect carnal hardware to the representation bus.”
The illustration is purely hypothetical. Signal spokesperson Jun Harada wrote successful an email: “Intel alerted america to this paper... and we were capable to verify that the CPUs that Signal uses are not impacted by the findings of this insubstantial and truthful are not susceptible to the stated attack.”
Key to the information and authenticity assurances of SGX is its instauration of what are called "enclaves," oregon blocks of unafraid memory. Enclave contents are encrypted earlier they permission the processor and are written successful RAM. They are decrypted lone aft they return. The occupation of SGX is to safeguard the enclave representation and artifact entree to its contents by thing different than the trusted portion of the CPU.
Enter ÆPIC Leak
Since 2018, researchers person poked astatine slightest 7 superior information holes successful SGX, immoderate of which wholly undermined the assurances Intel makes astir them. On Tuesday, a probe insubstantial publically identified a caller hole, which besides wholly breaks SGX guarantees successful astir 10th, 11th, and 12th procreation Intel CPUs. The chipmaker said it released mitigations that forestall the researchers’ proof-of-concept exploit from moving immoderate longer.
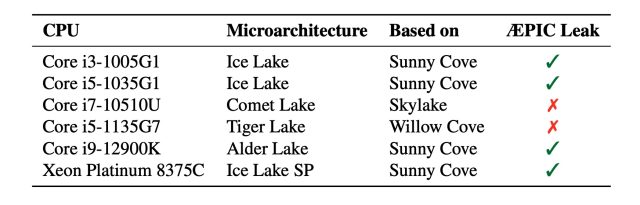
Enlarge / A database showing which Intel CPUs are vulnerable.
Borrello et al.
The vulnerability resides successful APIC, abbreviated for Advanced Programmable Interrupt Controller. APIC is simply a mechanics built into galore modern CPUs that manages and routes interrupts, which are signals generated by hardware oregon bundle that origin the CPU to halt its existent task truthful it tin process a higher-priority event. The researchers who discovered the flaw person named the vulnerability and their proof-of-concept exploit ÆPIC Leak.
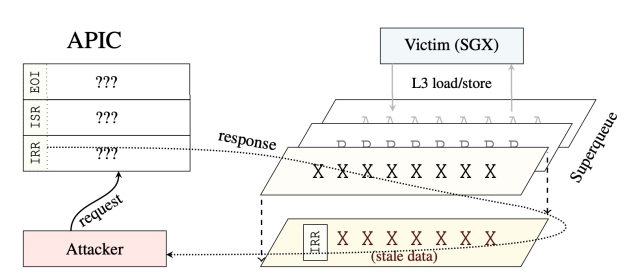
Enlarge / An overview of ÆPIC Leak.
Borrello et al.
The bug that makes ÆPIC Leak imaginable is what’s known arsenic an uninitialized representation read, which happens erstwhile representation abstraction isn't cleared aft the CPU is done processing it, causing the leak of aged information that is nary longer needed. Unlike erstwhile CPU flaws with names similar Spectre, Meltdown, Foreshadow, and RIDL/Fallout/ZombieLoad—which were the effect of transient execution creating side channels that revealed backstage data—ÆPIC Leak is an architectural flaw that resides successful the CPU itself.


 2 years ago
84
2 years ago
84