Enlarge / Nobody said getting basal entree to abstraction was going to beryllium easy.
Getting basal entree wrong 1 of Starlink's dishes requires a fewer things that are hard to travel by: a heavy knowing of committee circuitry, eMMC dumping hardware and skills, bootloader bundle understanding, and a customized PCB board. But researchers person proven it tin beryllium done.
In their speech "Glitched connected Earth by Humans: A Black-Box Security Evaluation of the SpaceX Starlink User Terminal," researchers astatine KU Leuven successful Belgium elaborate astatine Black Hat 2022 earlier this twelvemonth however they were capable to execute arbitrary codification connected a Starlink User Terminal (i.e., a crockery board) utilizing a custom-built modchip done a voltage responsibility injection. The speech took spot successful August, but the researchers' slides and repository person precocious made the rounds.
There's nary contiguous threat, and the vulnerability is some disclosed and limited. While bypassing signature verification allowed the researchers to "further research the Starlink User Terminal and networking broadside of the system," slides from the Black Hat talk enactment that Starlink is "a well-designed merchandise (from a information standpoint)." Getting a basal ammunition was challenging, and doing truthful didn't unfastened up evident lateral question oregon escalation. But updating firmware and repurposing Starlink dishes for different purposes? Perhaps.
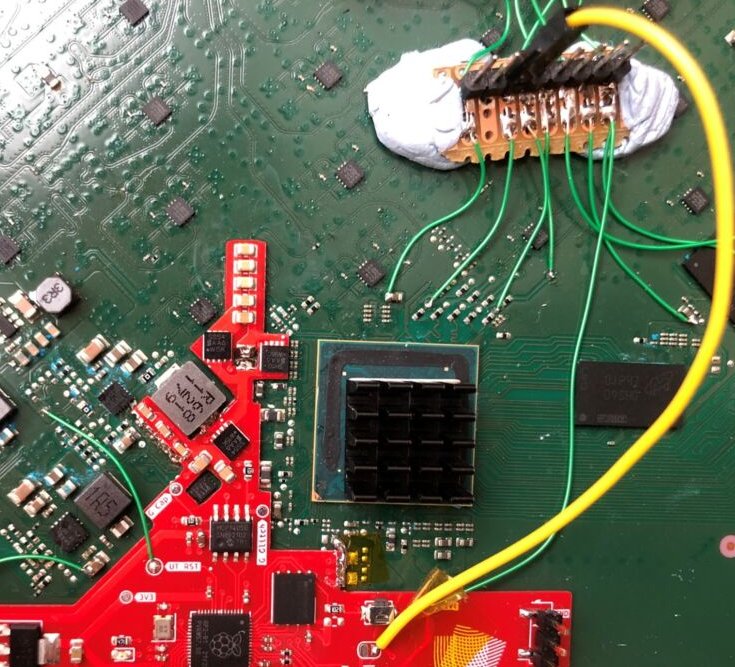
Still, outer information is acold from simply theoretical. Satellite supplier Viasat saw thousands of modems knocked offline by AcidRain malware, pushed by what astir measure to beryllium Russian authorities actors. And portion the KU Leuven researchers enactment however unwieldy and tricky it would beryllium to connect their customized modchip to a Starlink terminal successful the wild, galore Starlink terminals are placed successful the astir distant locations. That gives you a spot much clip to disassemble a portion and marque the much than 20 fine-point soldering connections elaborate successful descent images.
-
Reading from eMMC trial points to extract and spot Starlink's firmware.
-
The basal plan of the Starlink intruder modchip, with a Pi-designed processor astatine its halfway
-
Nobody said getting basal entree to abstraction was going to beryllium easy.
-
How to trial your outer information proof-of-concept erstwhile you enactment wrong a university.
It's not casual to summarize the galore techniques and disciplines utilized successful the researchers' hardware hack, but present is an attempt. After immoderate high-level committee analysis, the researchers located trial points for speechmaking the board's eMMC storage. Dumping the firmware for analysis, they recovered a spot wherever introducing errant voltage into the halfway strategy connected a spot (SoC) could modify an important adaptable during bootup: "development login enabled: yes." It's slow, it lone works occasionally, and the voltage tampering tin origin tons of different errors, but it worked.
The modchip utilized by the researchers is centered astir a RaspberryPi RP2040 microcontroller. Unlike astir Raspberry Pi hardware, you tin inactive seemingly bid and person the halfway Pi chip, should you embark connected specified a journey. You tin work much astir the firmware dumping process successful the researchers' blog post.


 2 years ago
40
2 years ago
40