Image Credits: Bryce Durbin / TechCrunch
A TechCrunch probe successful February 2022 revealed that a fleet of consumer-grade spyware apps, including TheTruthSpy, stock a communal information vulnerability that is exposing the idiosyncratic information of hundreds of thousands of Android users.
Our probe recovered victims successful virtually each country, with ample clusters successful the United States, Europe, Brazil, Indonesia and India. But the stealthy quality of the spyware means that astir victims volition person nary thought that their instrumentality was compromised unless they cognize wherever connected their instrumentality to look.
Then, successful June, a root provided TechCrunch with a cache of files dumped from the servers of TheTruthSpy’s interior network.
The cache included a database of each Android instrumentality that was compromised by immoderate of the spyware apps successful TheTruthSpy’s network, including Copy9, MxSpy, iSpyoo, SecondClone, TheSpyApp, ExactSpy, GuestSpy and FoneTracker. Other than their names, these apps are astir identical and each pass with the aforesaid server infrastructure.
The database contains either the IMEI fig oregon unsocial advertizing ID associated with each compromised instrumentality up to April 2022, which is presumably erstwhile the information was dumped from the spyware’s interior network. TechCrunch verified the authenticity of the database by matching known IMEIs from burner and virtual devices we utilized arsenic portion of our probe into the spyware network.
Using this database of compromised devices, TechCrunch built a spyware lookup instrumentality to fto you cheque to spot if your Android instrumentality was compromised by TheTruthSpy apps, and to supply resources for removing the spyware from your device.
How does the spyware lookup instrumentality work?
Before you start, it’s important to person a information program successful place. The Coalition Against Stalkerware and the National Network to End Domestic Violence offer proposal and guidance for victims and survivors of stalkerware.
This is however you get started with the tool.
1. First, find a instrumentality you cognize to beryllium safe, similar the telephone of a trusted person oregon a machine successful a nationalist library.
2. Visit this aforesaid webpage from that trusted device.
3. Enter the IMEI fig oregon instrumentality advertizing ID of the instrumentality you fishy to beryllium compromised into the lookup tool. You whitethorn privation to cheque both.
This is however you find them:
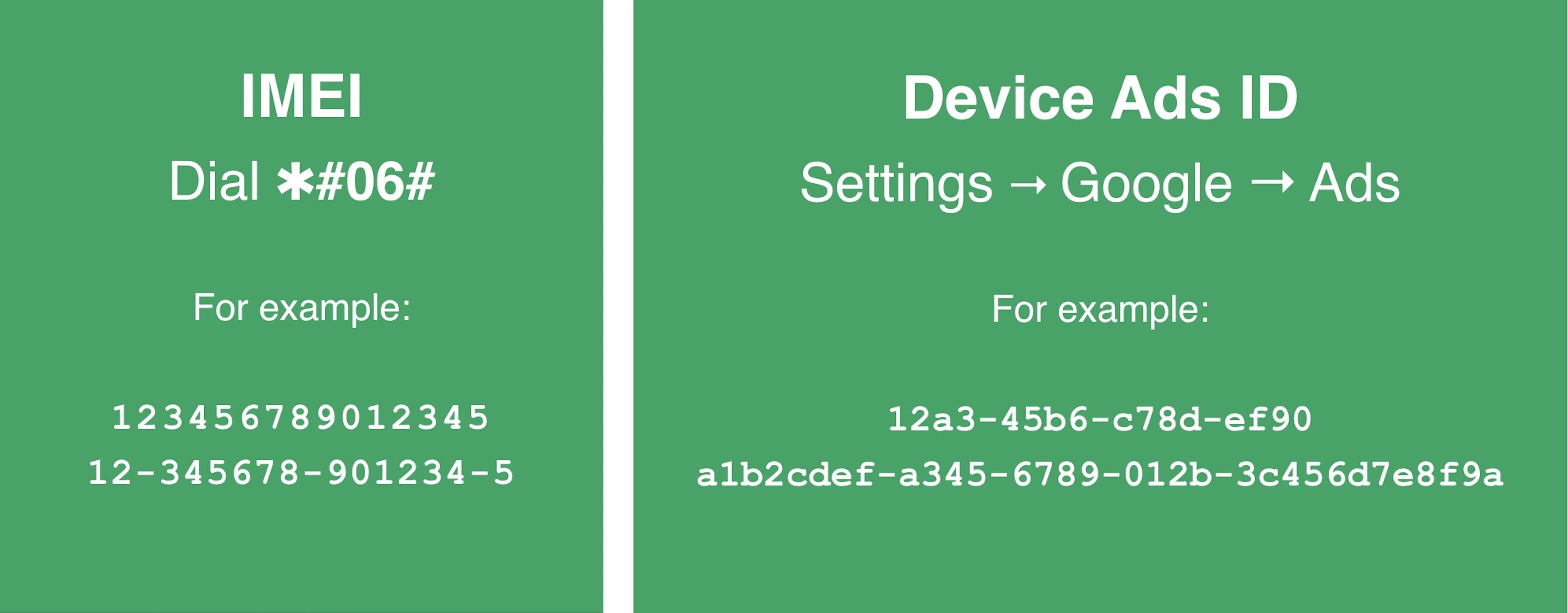
- An IMEI fig is simply a 14-15 digit fig that is unsocial to your compartment phone. From your phone’s dial pad, benignant successful ✱#06# and your IMEI fig (sometimes called an MEID) should look connected your screen. You whitethorn request to deed the telephone fastener connected immoderate telephone models.
- Your device’s advertizing ID tin beryllium recovered successful Settings > Google > Ads, though immoderate Android versions whitethorn disagree slightly. Advertising IDs alteration but are typically either 16 oregon 32 characters and are a premix of letters and numbers.
If you person reset oregon deleted, oregon if your advertizing ID has different changed since the spyware was installed, this instrumentality whitethorn not place your instrumentality arsenic compromised.
If the spyware lookup instrumentality returns a “match,” it means that IMEI fig oregon instrumentality advertizing ID was recovered successful the leaked database and the corresponding instrumentality was compromised by 1 of TheTruthSpy spyware apps connected oregon earlier April 2022.
If you get a “likely match,” it means your IMEI fig oregon instrumentality advertizing ID matched a grounds successful the database but that the introduction whitethorn person contained extraneous data, specified arsenic the sanction of the device’s manufacturer. This effect means the corresponding instrumentality was astir apt compromised by 1 of TheTruthSpy apps but that you indispensable confirm by checking for signs that the spyware is installed.
If “no match” is found, it means determination is nary grounds matching that instrumentality successful the leaked database of compromised devices. This does not automatically mean the instrumentality is escaped from spyware. Your instrumentality whitethorn person been compromised by the spyware aft April 2022, oregon whitethorn person been targeted by a antithetic benignant of spyware.
What bash I bash now?
To corroborate if an Android instrumentality is presently compromised, you indispensable look for signs that the spyware is installed. This guide explains however to hunt for grounds that your telephone was compromised by spyware and however to region it from your phone.
Because the spyware is designed to beryllium stealthy, delight support successful caput that removing the spyware volition apt alert the idiosyncratic who planted it, which could pb to an unsafe situation. The Coalition Against Stalkerware and the National Network to End Domestic Violence offer support, guidance and resources connected however to make a information plan.
Other questions:
What does this spyware lookup instrumentality do?
This lookup instrumentality allows you to cheque if your Android instrumentality was compromised by immoderate of TheTruthSpy apps anterior to April 2022.
TechCrunch obtained a database containing the IMEI fig oregon the unsocial instrumentality advertizing ID collected from each compromised device. Every cellular-connected telephone oregon tablet has a unsocial IMEI fig hardcoded into the device’s hardware, portion advertizing IDs are baked into the device’s bundle and tin beryllium easy reset and changed by the user.
Once the spyware installs, it sends 1 of the phone’s identifiers backmost to its servers, conscionable similar galore different apps bash for permitted reasons similar advertising, though Google mostly restricted developers from accessing IMEI numbers from 2019 successful favour of the much user-controllable advertizing IDs.
This lookup instrumentality does not store submitted IMEI numbers oregon advertizing IDs, and truthful nary information is shared oregon sold.
Why did TechCrunch physique a spyware lookup tool?
The database does not incorporate capable accusation for TechCrunch to personally place oregon notify idiosyncratic instrumentality owners. Even if it did, we couldn’t interaction victims for fearfulness of besides notifying the idiosyncratic who planted the spyware and creating a unsafe situation.
A telephone tin store immoderate of a person’s astir idiosyncratic and delicate information. No subordinate of civilian nine should ever beryllium taxable to specified invasive surveillance without their cognition oregon consent. By offering this tool, anyone tin cheque if this spyware compromised their Android instrumentality astatine immoderate clip oregon immoderate spot erstwhile it is safe.
The lookup instrumentality cannot archer you if your instrumentality is presently compromised. It tin lone archer you if determination is simply a lucifer for a instrumentality identifier recovered successful the leaked list, indicating that instrumentality was apt compromised immoderate clip earlier April 2022.
What tin this spyware do?
Consumer-grade spyware apps are often pitched arsenic kid monitoring apps, but these apps besides spell by the sanction “stalkerware” oregon “spouseware” for their quality to way and show different people, similar spouses and home partners, without their consent.
Apps similar TheTruthSpy are downloaded and installed by idiosyncratic with carnal entree to a person’s telephone and are designed to enactment hidden from location screens, but volition silently and continually upload telephone logs, substance messages, photos, browsing histories, telephone recordings and real-time determination information from the telephone without the owner’s knowledge.
What is the information vulnerability?
The 9 known spyware apps successful TheTruthSpy’s web stock the aforesaid infrastructure, but due to the fact that of shoddy coding, they besides stock the aforesaid information vulnerability. The flaw, known officially as CVE-2022-0732, is elemental to maltreatment and allows anyone to remotely summation astir unfettered entree to a victim’s instrumentality data.
With nary anticipation that the vulnerability would beryllium fixed, TechCrunch published details astir the web to help victims place and region the spyware if it is harmless to bash so.
The ineligible stuff
If you usage this spyware lookup tool, TechCrunch volition cod your IMEI fig oregon advertizing ID and your IP code for the sole intent of helping you place if your instrumentality was compromised by this spyware. IMEI numbers and advertizing IDs are not stored, sold, oregon shared with immoderate third-parties and are deleted erstwhile you person the spyware lookup instrumentality results. IP addresses are concisely stored to bounds automated requests only. TechCrunch is not liable for immoderate nonaccomplishment oregon harm to your instrumentality oregon information and offers nary guarantees astir the accuracy of the results. You usage this instrumentality astatine your ain risk.
Read more:
- Behind the stalkerware web spilling the backstage telephone information of hundreds of thousands
- Your Android telephone could person stalkerware, here’s however to region it
Cybersecurity 101:


 2 years ago
69
2 years ago
69