Researchers judge hackers with connections to the North Korean authorities person been pushing a Trojanized mentation of the PuTTY networking inferior successful an effort to backdoor the web of organizations they privation to spy on.
Researchers from information steadfast Mandiant said connected Thursday that astatine slightest 1 lawsuit it serves had an worker who installed the fake web inferior by accident. The incidental caused the leader to go infected with a backdoor tracked by researchers arsenic Airdry.v2. The record was transmitted by a radical Mandiant tracks arsenic UNC4034.
"Mandiant identified respective overlaps betwixt UNC4034 and menace clusters we fishy person a North Korean nexus," institution researchers wrote. "The AIRDRY.V2 C2 URLs beryllium to compromised website infrastructure antecedently leveraged by these groups and reported successful respective OSINT sources."
The menace actors posed arsenic radical recruiting the worker for a occupation astatine Amazon. They sent the people a connection implicit WhatsApp that transmitted a record named amazon_assessment.iso. ISO files person been progressively utilized successful caller months to infect Windows machines because, by default, double-clicking connected them causes them to equine arsenic a virtual machine. Among different things, the representation had an executable record titled PuTTY.exe.
PuTTY is an unfastened root unafraid ammunition and telnet application. Secure versions of it are signed by the authoritative developer. The mentation sent successful the WhatsApp connection was not signed.
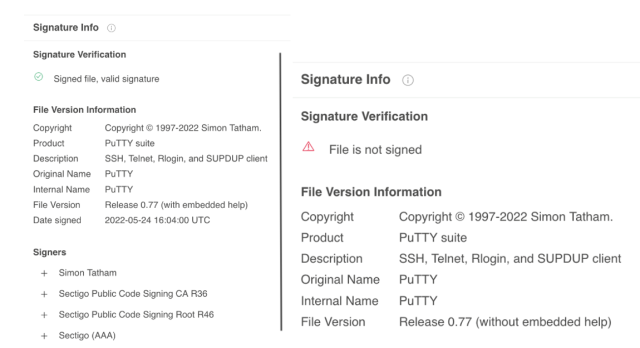
Mandiant
The executable record installed the latest mentation of Airdry, a backdoor the US authorities has attributed to the North Korean government. The US Cybersecurity and Infrastructure Security Agency has a statement here. Japan's assemblage exigency effect squad has this statement of the backdoor, which is besides tracked arsenic BLINDINGCAN.


 2 years ago
55
2 years ago
55